ExploitChance is evaluated through controlled, provider-operated pilots.
Commercial terms are defined following technical and operational assessment.
For evaluation enquiries, contact admin@pentest.es.
Anti Phishing (GMail links protection)
Fully Gmail-compatible, it modifies HTML links to allow access only to those permitted by policy, all within an unbreakable (seL4®) virtual environment.
OpenFileSecure (Endpoint or Server)
Execute high-risk workloads in a secure, seL4®-based local virtual environment, ensuring immunity to 0-day vulnerabilities in formats such as PDF, ZIP, RAR, 7z, TAR, RPM, ISO, BZ2, GZ, XZ, AR, VMDK, VHDX, VHD, ARJ, CPIO, CRAMFS, EXT, FAT, GPT, QCOW2, SQUASHFS, WIM, XAR, and HFS.
Inspector Firewall (Protect HTTPS traffic)
Endpoint-based SSL inspection: 1) Eliminates single points of attack at the corporate firewall 2) Infinitely scalable 3) Unrivaled Throughput
Contact us for a full demo with our hardware based appliance
Protected Browsers
Regardless of the browsers your users choose, our Windows KERNEL driver sandbox ensures comprehensive protection.
Trust by Risk
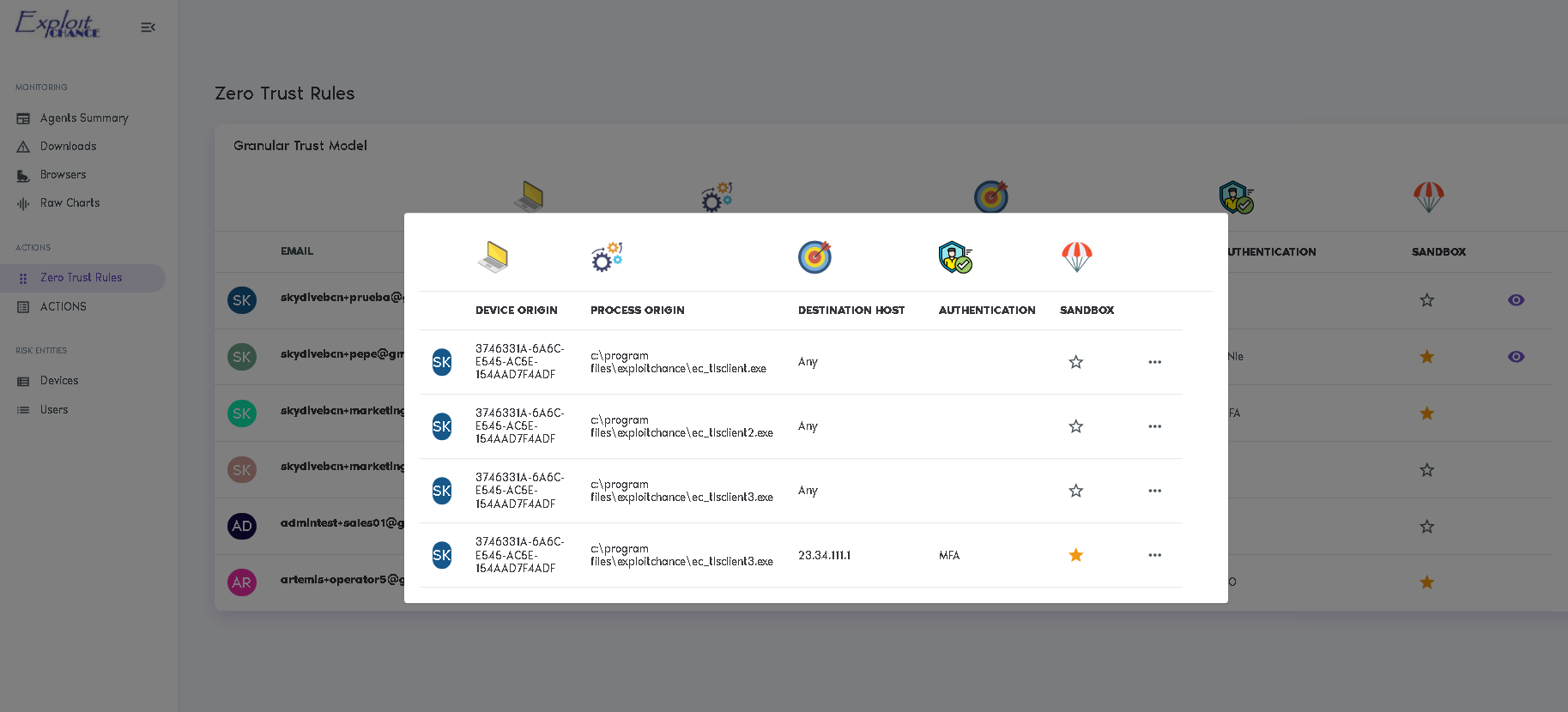
User and Endpoint Risk dynamically adjusts ZTNA in real time, automatically defining access controls.
Secure-by-Design RC
Dual-use technology featuring passwordless access, formal security (seL4®), Rust, OCaml, and military-grade standards.
Endpoint AI
Our AI workloads handling sensitive or personal data run entirely on endpoints, ensuring no data is shared with third parties and eliminating data leaks (100% privacy compliant). AI is distributed across all endpoints.
ExploitChance focuses on the primary threat: malware that reaches the computer, whether through email, downloads, shares, or USB devices.
We protect the desktop at the design level, ensuring that exploits are rendered ineffective from the start.
Unlike traditional solutions, we don’t rely on software behavior or signatures; we eliminate the threat at its core, making exploits useless before they can do harm.
Our KERNEL-based sandbox and ENDPOINT SSL INSPECTION provide added protection over all your browsers.
A transparent anti-phishing solution intercepts webmail links (i.e. Gmail) and enforces corporate security policies.
A robust and transparent defense against various web interception attacks —including Browser-in-the-Middle, Man-in-the-Middle, and Machine-in-the-Middle— through the enforcement of client certificates, a dedicated, locally sandboxed browser and Zero Trust policies.
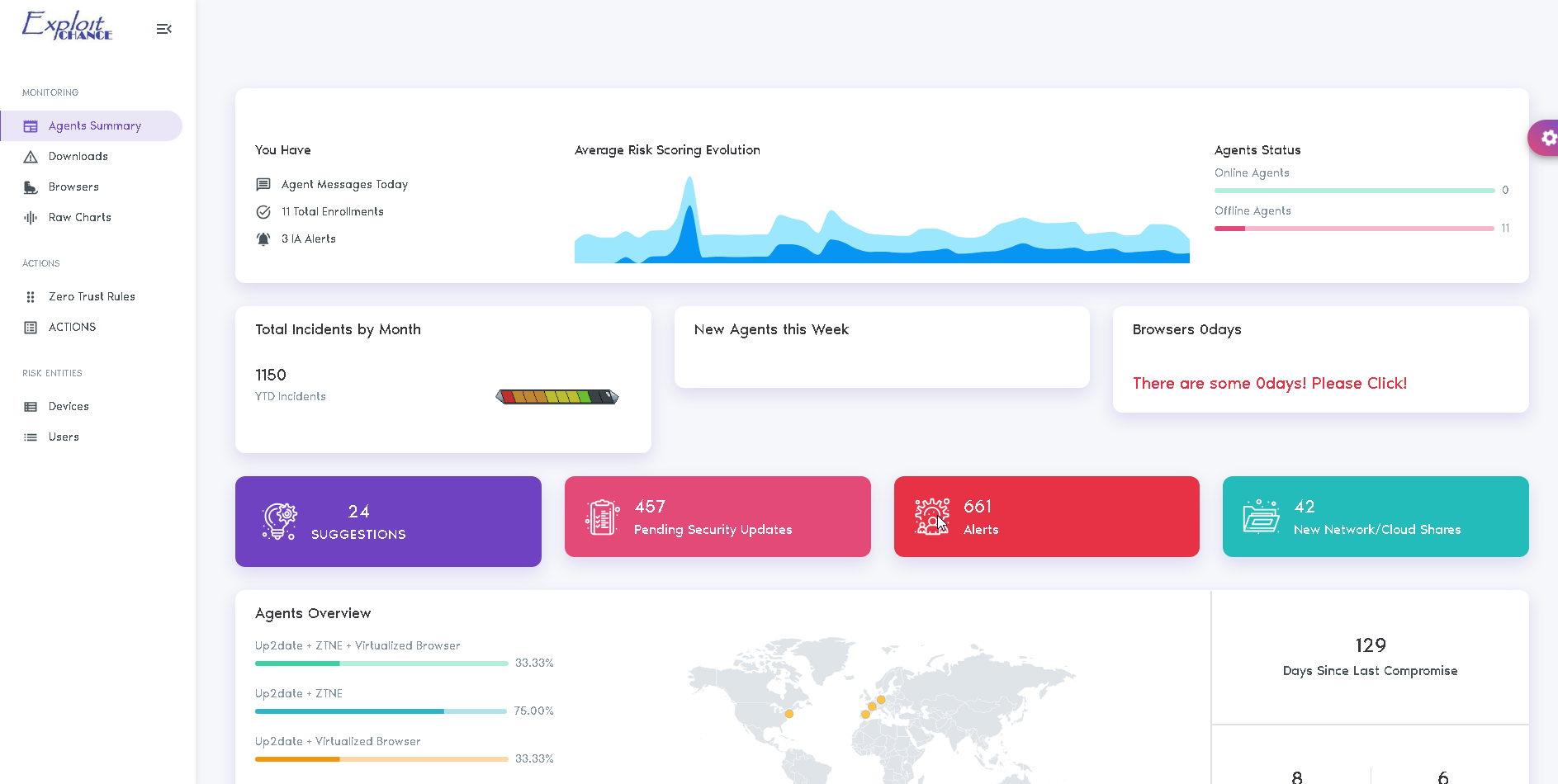
Improve the global risk aware posture
MONITOR AND STOP RISKY BEHAVIOR
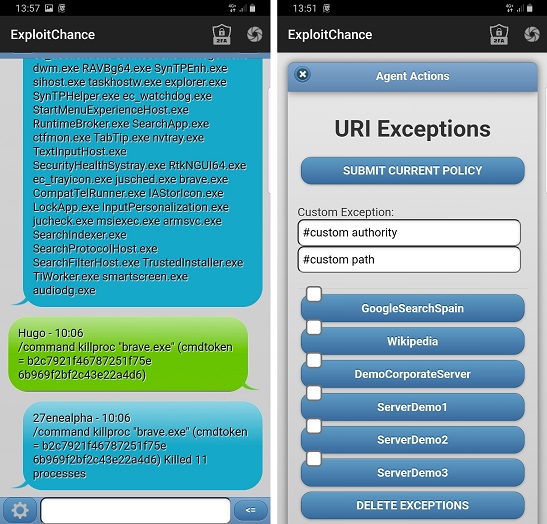
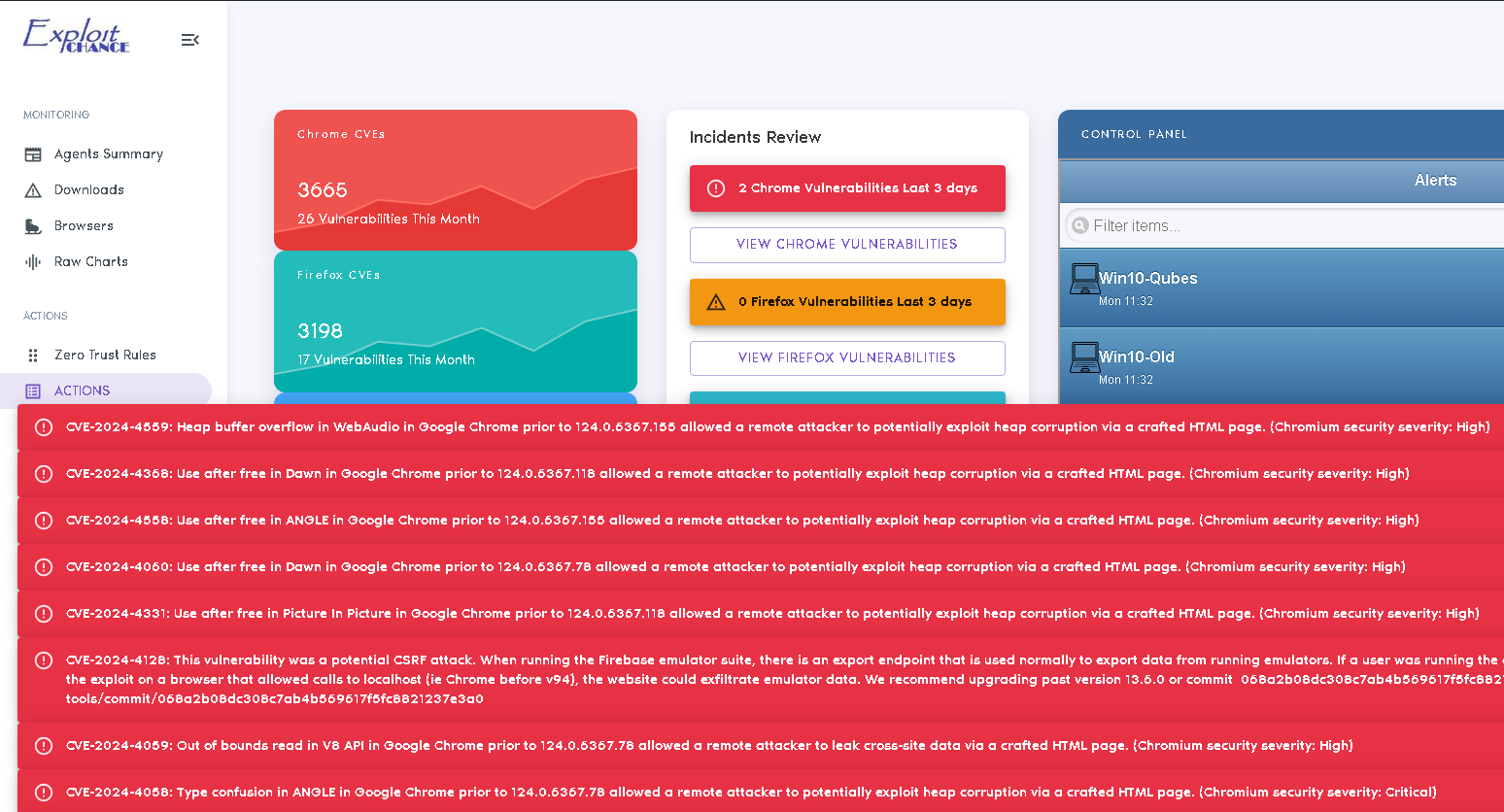
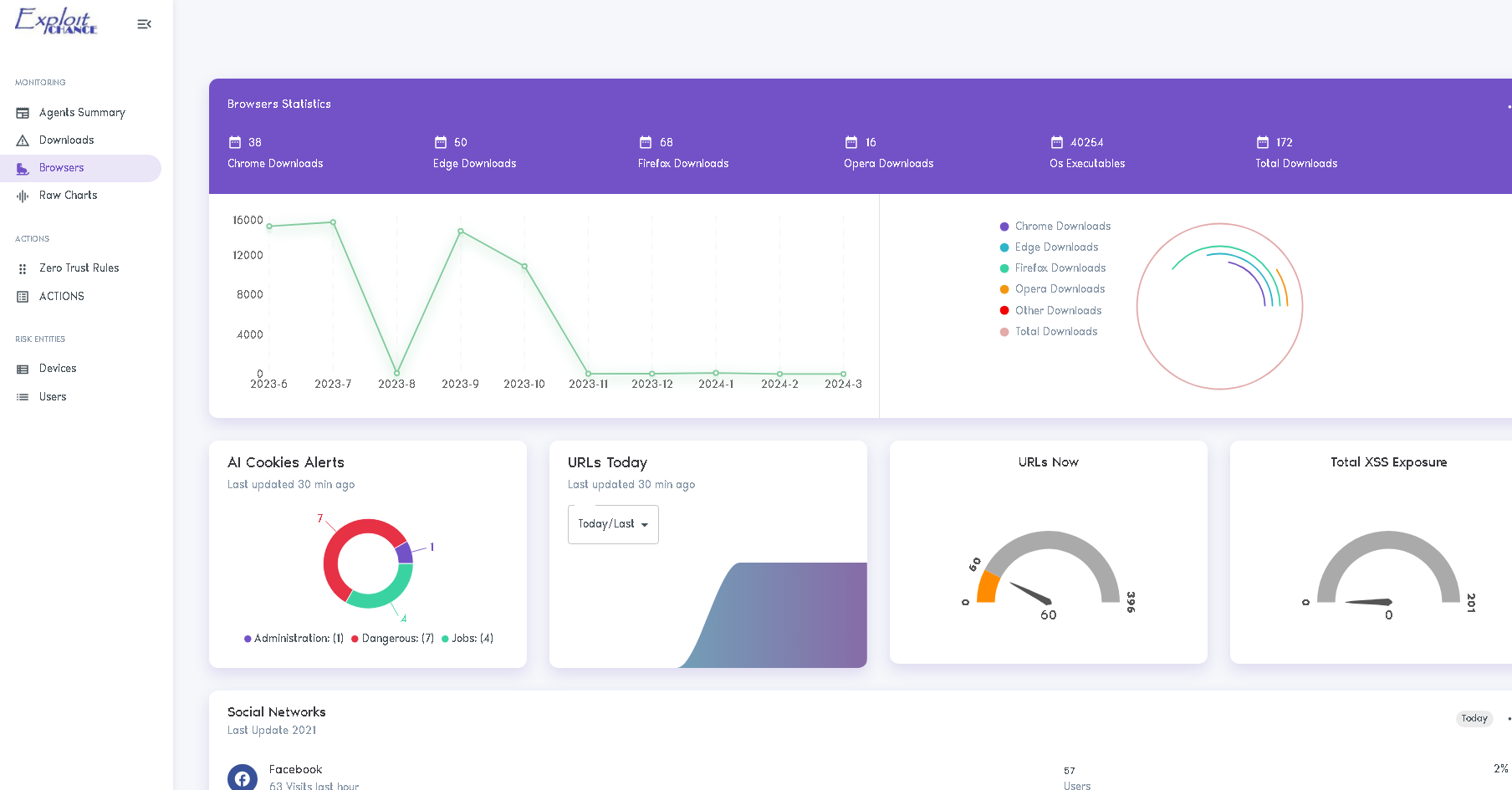
ExploitChance provides visibility into your users' activities, including browsing, downloads, sharing, and more.
It also enables you to warn or block users when they engage in risky behavior that could expose the company.
EC integrates with any cloud FWaaS or EDR, detecting risky user actions and dynamically reconfiguring Zero Trust and other security solutions.
Protect Privacy
TOTAL PRIVACY COMPLIANCE
The ExploitChance solution is designed to never compromise user or corporate privacy. It's not just a promise; our architecture makes misuse of data impossible.
The backend environment does not receive any sensitive or private information, only generic telemetry data.
All handling of sensitive information (if any) is managed exclusively at the endpoint (agent), with personal data processing occurring locally on the user's device.
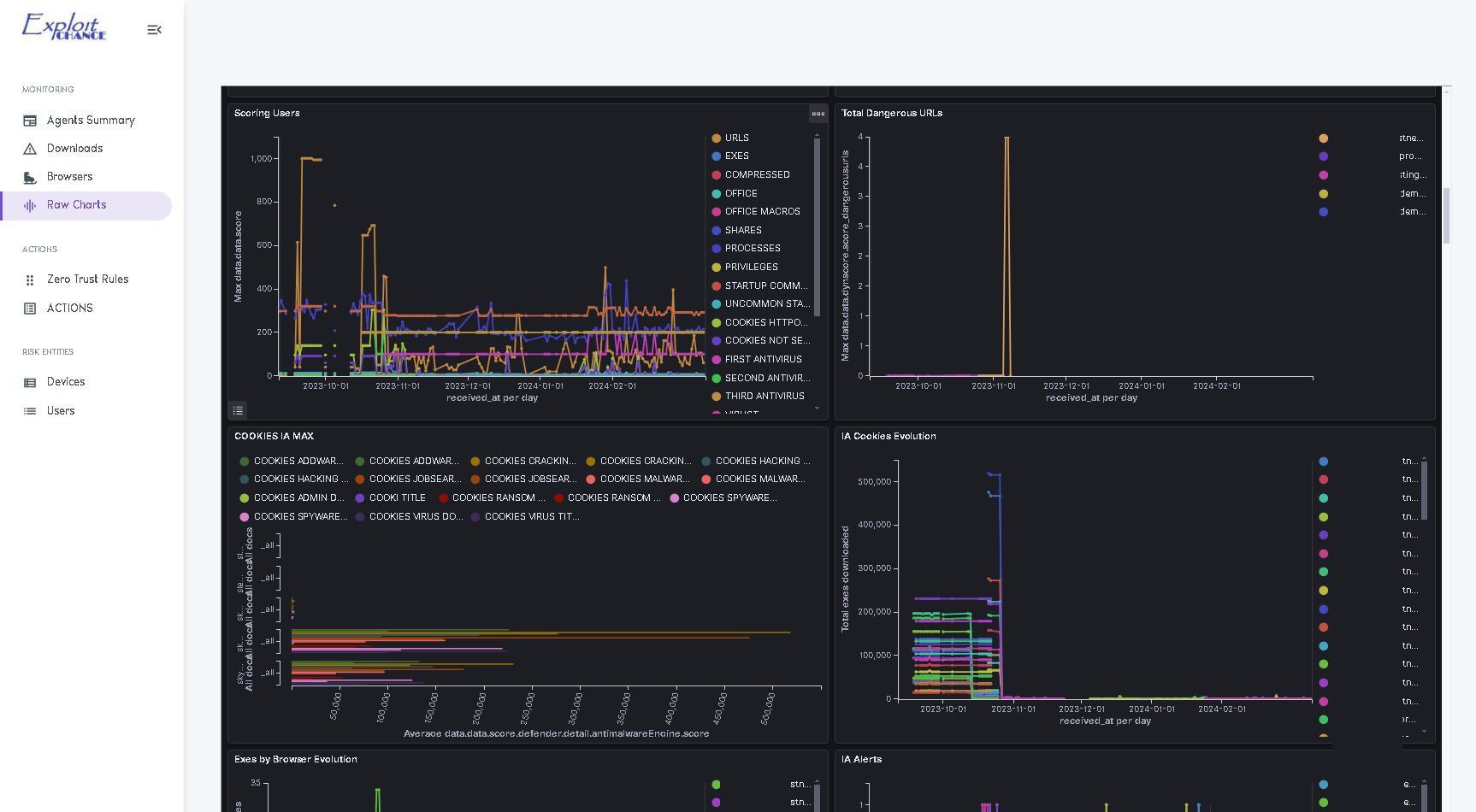
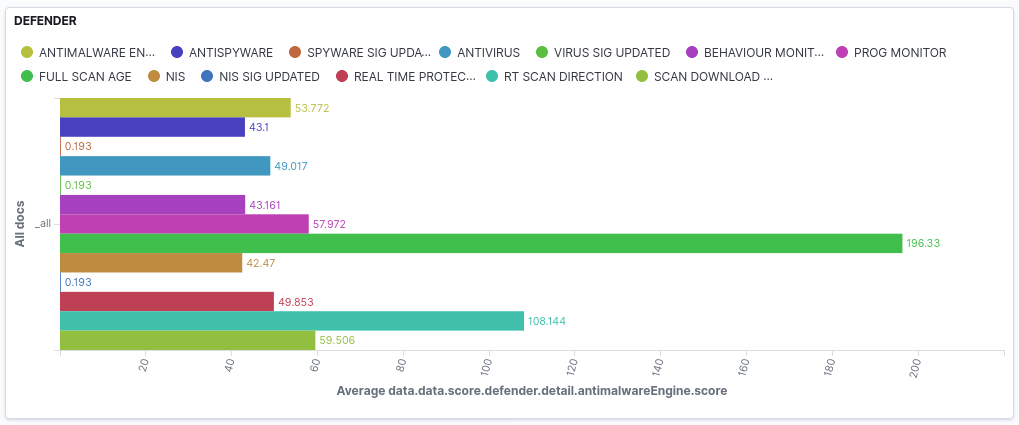
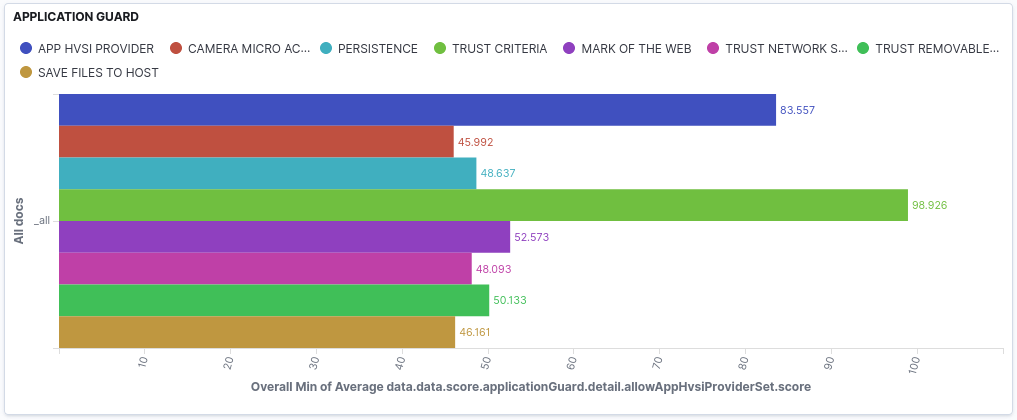
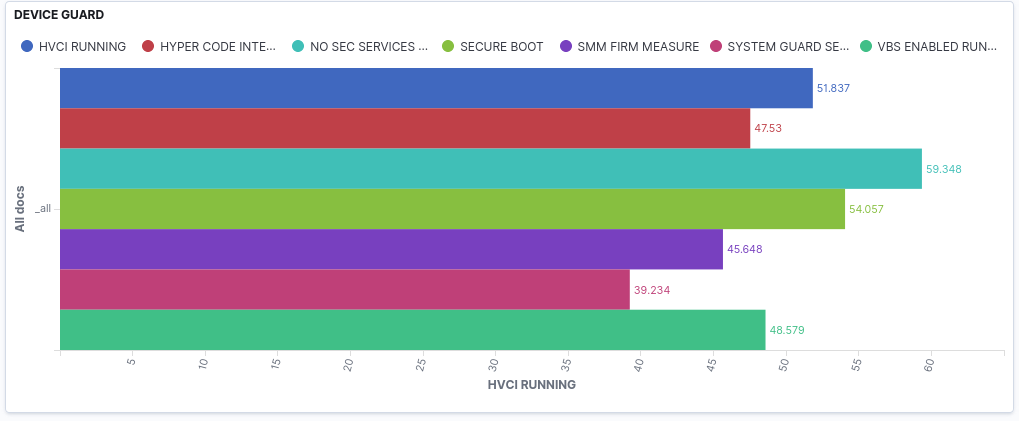
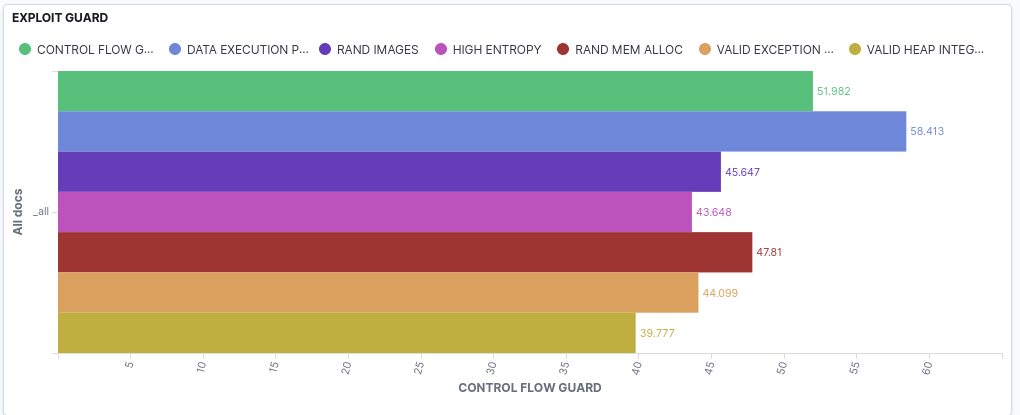
EXAMPLE OF HARDENING TELEMETRY
Beyond privacy standards
Forget about data leaks—no sensitive data is stored in the cloud.
Scalable Solution
With no single point of failure, resilience is guaranteed.
Fully mobile-ready
Allow administrators to benefit from the convenience and speed of mobile management, enabling both SoC and on-site or remote admins to sync for quicker crisis response.
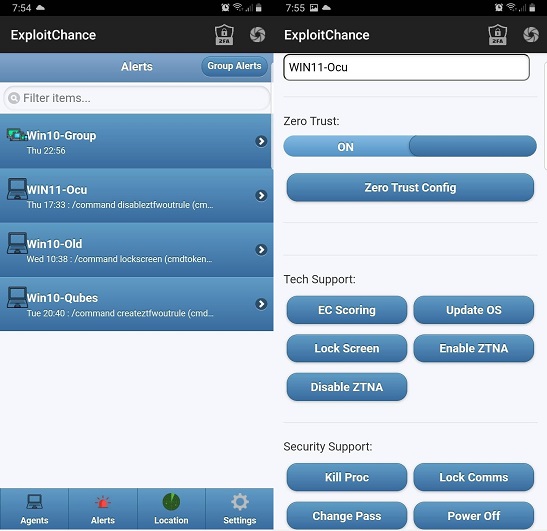
Give your security teams real time control with a mobile app
Reduce incident response time with ultra-secure remote control of monitored devices, enabling swift action when needed.
The app allows admins to receive optional real-time alerts, designed to speed response time in emergency cases, and take immediate action directly on affected devices without relying on SoC operators.
In the evolving work environment with more remote workers, including security administrators, it makes sense to offer mobile security administration capabilities.
All critical operations are safeguarded by strict security controls, ensuring that no mobile admin device can be used as an entry point into the company.
Security
Is it secure?
EXPLOIT CHANCE operates seamlessly and securely in any environment, designed with 'human error-proofing' in mind. Regardless of the system administrator's experience, EXPLOIT CHANCE ensures security from the start, covering every aspect and leaving no room for mistakes. Security should be simple.
MFA, 4 EYES, ETC
Critical operations are enforced by MILITARY GRADE AUTH mechanisms
FORMAL SECURITY
Critical modules are built on top of seL4® a microkernel formally verifiied
SECURITY by DESIGN
Our design posture is always to assume the worst case scenario
RUST
Our software is built with Rust, a language designed to be memory safe
You can trust us.